Networking and IT-Security
Computers are nowadays mainly responsible for our connections. However, being connected to a network exposes us to many different threats and high risks from attackers. Therefore, we must have an understanding of networks to be able to defend ourselves against such attackers.
In this tutorial, we will explain the most important topics of networking that are important for IT-Security.
What is the Open Systems Interconnection model (OSI model)?
This is a conceptual model that helps us to understand how the data travels across the network between two or more systems.
This model divides the data flow into seven abstract layers:
| Layer name | Description | Example |
|---|---|---|
| 7. Application Layer | The OSI application layer and the end-user interface are directly connected with an application software. | SSH, FTP, HTTP, SMTP,IMAP |
| 6. Presentation Layer | Data representation, encryption | SSL, TLS |
| 5. Session Layer | Session management | SCP |
| 4. Transport Layer | Reliable delivery of data | TCP, UDP |
| 3. Network Layer | Routing and delivery from/to nodes | IPv4, IPv6, ICMP |
| 2. Data Link Layer | Provides peer-to-peer data transfer and acts as a link between two connected peers. | MAC, HDLC |
| 1. Physical Layer | Responsible for sending and receiving raw bitstreams and packets over a physical medium | DSL, Ethernet, CAT5 |
Open Systems Interconnection model (OSI model)
What is the TCP/IP model?
TCP/IP protocols are a whole suite of communication protocols that are all based on the Internet Protocol (IP). The basic features of the TCP/IP protocol suite were defined before the standardization of the OSI reference model and deviated from this model. There were seven layers in the OSI reference model, but the TCP/IP protocol suite is based here on a four-layers model:
| Layer name | Description | Example |
|---|---|---|
| Application Layer | The end-user interface interacts with network applications | HTTP, FTP, SMTP, DNS |
| Transport Layer | Delivery and multiplexing of data to network applications | TCP, UDP |
| Internet Layer | Routing data and delivery from/to nodes | IP, ICMP |
| Link Layer | Provides peer-to-peer data transfer and acts as a link between two connected peers. | ARP, PPP |
TCP/IP model
What is the difference between the OSI model and the TCP/IP model?
We want to know now how both of the models are related to each other. The table below shows us the relation between both models:
| TCP/IP Model Layer | Equivalent Layer in OSI Model |
|---|---|
| Application Layer | Application Layer, Presentation Layer, Session Layer |
| Transport Layer | Transport Layer |
| Internet Layer | Network Layer |
| Link Layer | Data Link Layer, Physical Layer |
Difference between the OSI model and the TCP/IP model?
Protocols:
User Datagram Protocol (UDP)
It’s a protocol based on the transport layer. The header size in UDP is 8 Bytes.
This protocol has no guarantee that data that has been sent is actually delivered. It also has no guarantee of ordering or duplicate protection.
An advantage of UDP is that it does not take time to establish a connection or correct errors and generates no overhead, hence it is faster than the TCP protocol.
It is usually used for performance-critical applications like DNS and DHCP.
Transmission Control Protocol (TCP)
It’s a protocol based on the transport layer. The header size in TCP is 20 bytes.
In this Protocol, a valid connection between systems is established before data is transmitted.
TCP guarantees ordered data transfer, retransmission of lost packages, and Flow control therefore, TCP takes more time to transfer data compared to UDP.
Applications that require high reliability for data transfer make use of TCP like SSH and FTP.
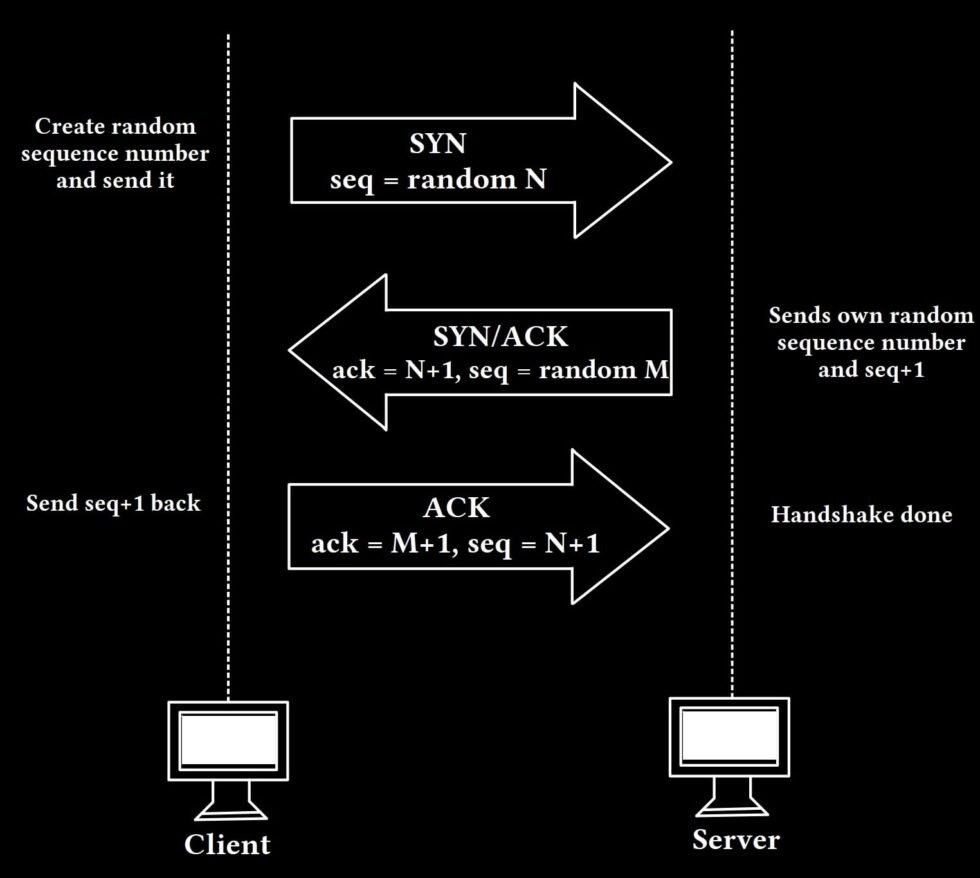
How does TCP Handshake work (3-Way Handshake)?
We have two hosts (client and server) and we want to establish a connection between the two. In order for the connection to be established, the client generates a random sequence number (N) and sends it to the server as an SYN packet.
The server sends an SYN/ACK packet to establish the connection. In the ACK part of the message, the server confirms the sequence number of the client plus one (N+1) and also sends its own sequence number (M) for the SYN part.
The client now confirms the receiving by confirming the sequence number (M+1) and he sends also his own old confirmed sequence number (N+1).
Internet Control Message Protocol (ICMP)
This protocol is used to exchange information between network devices and to exchange error messages. This protocol is not implemented by applications and is not used to directly exchange data between devices.
An example would be the ping program, which sends an ICMP-Echo-Request-Packet and waits for an Echo-Response to check whether a computer can be reached and how high the network latency is.
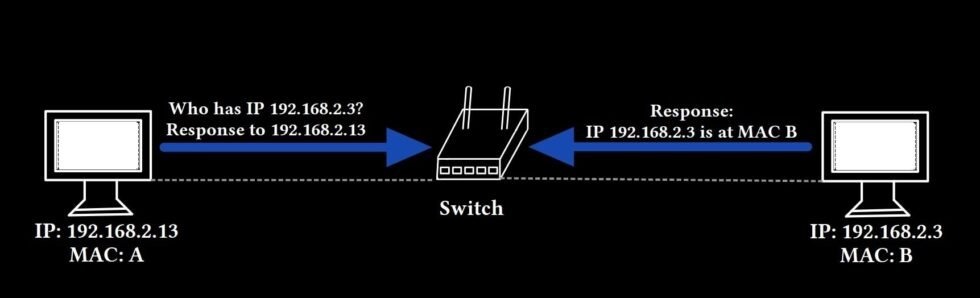
Address Resolution Protocol (ARP)
ARP maps network addresses (IP) to physical addresses (MAC) and RARP (Reverse Address Resolution Protocol) does the opposite. The mapping is stored in the ARP cache on the host or switch.
Address Resolution Protocol (ARP)
Dynamic Host Configuration Protocol (DHCP)
There are two types of given IP addresses: Static IP and dynamic IP.
A static IP address stays persistent no matter how many times a computer disconnects and reconnects to the network.
A dynamic IP address is allocated to a computer only for a particular session/duration. So when a computer gets an IP address and connects to a network and then disconnects, it gets a new IP address after the new connection.
The DHCP protocol is responsible for dynamically allocating IP addresses to systems. If a computer doesn’t want a static IP, it communicates with the DHCP server to get a temporary IP address for that specific session.
Domain Name System (DNS)
This protocol translates domain names to actual IP addresses.
When we type a website name in our browser, the browser asks the DNS server what IP address the website has to connect with that IP address.
Why is Networking Important for IT Security?
We have just learned many protocols but these protocols are not perfect. A hacker can easily exploit these protocols. There are several attacks a hacker can perform against these protocols and against a network:
- Network Sniffing
- ARP Spoofing
- TCP Connection Spoofing
- TCP Hijacking
- Denial of Service Attack (DoS)
- Distributed DoS Attack (DDoS)
- TCP Syn Flooding
- DNS Cache Poisoning
We will explain in more detail about each individual attack in future posts on our website.