What is Cryprography
Cryptography exists everywhere in our lives (e.g. surfing the web with HTTPS, messaging apps like WhatsApp and WiFi).
We can consider cryptography as the heart of IT security because without cryptography, IT security does not work.
In this article, you will learn all the basics of Cryptography.
The generic term for cryptography is Cryptology, and this term is divided into:
- Cryptography: Deals with data security (e.g. Protocols, Symmetric, and Asymmetric Cryptography)
- Cryptanalysis: Deals with breaking cryptographic methods (e.g. Known Ciphertext attack, Brute Force attack, and Social Engineering)
What does cryptography do?
We have data (e.g. a text) that we want to send securely to a friend. To do this, we apply cryptographic encryption methods to the text to encrypt it. After the text has been encrypted, we can send it to the friend. However, our friend cannot read the text either because it is encrypted. They use cryptographic decryption methods to decrypt the text and be able to read it.
So the main goal of cryptography is to make our data safe.
Common Figures in Cryptography
- Alice: The first person who wants to exchange sensitive information. Bob: The second person who wants to exchange sensitive information.
- Eve: A person who can listen to the messages between Alice and Bob but can’t modify the messages (passive attacker).
- Mallory: A person who can listen to the messages between Alice and Bob, modify the messages, and delete them (active attacker)
How do Symmetric and Asymmetric Encryption work?
How do Symmetry and Asymmetric Encryption work?
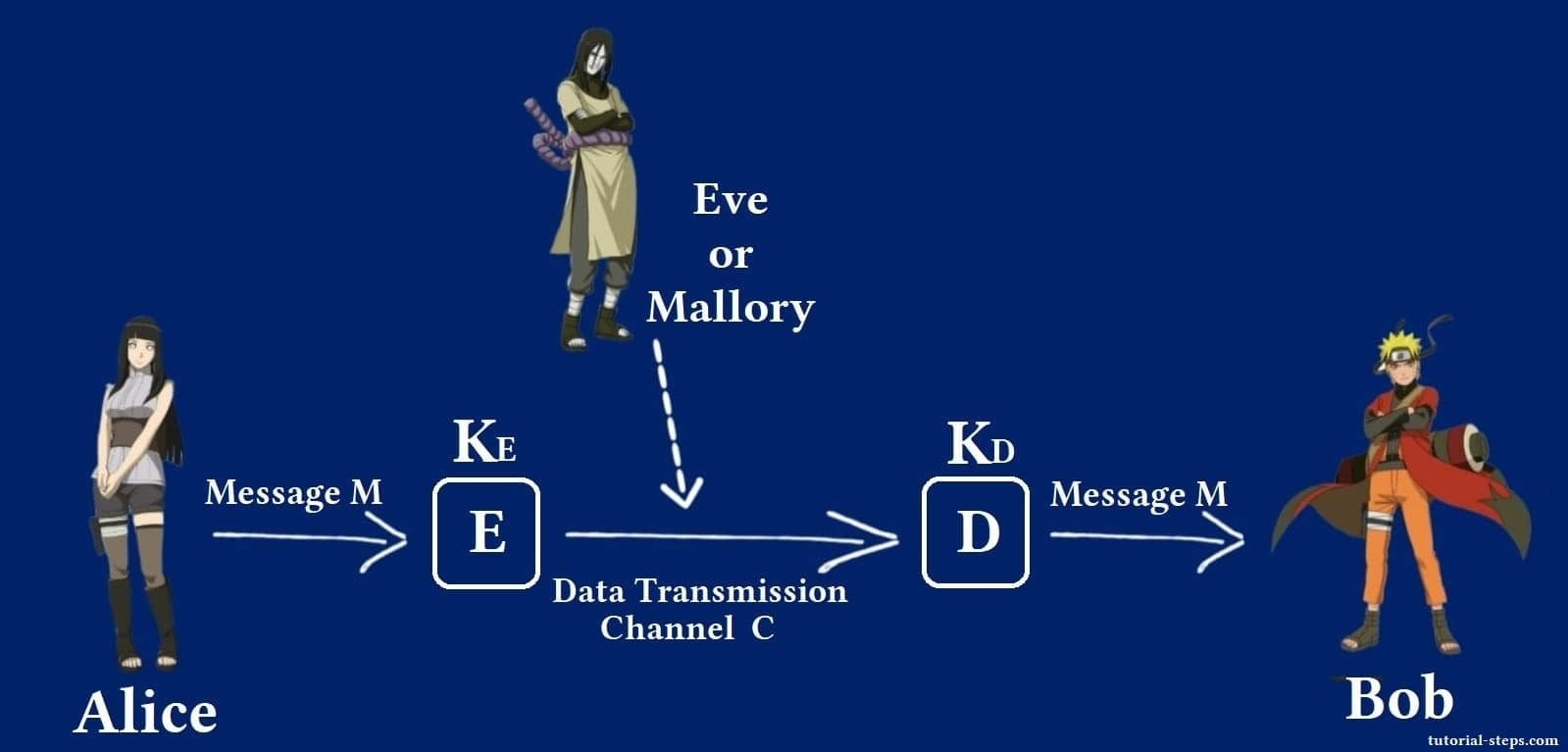
- Alice wants to send a plaintext message (M) to Bob.
- To do that, she applies an encryption algorithm (E) to this plaintext (M).
- To encrypt (M) into a ciphertext, (E) needs a key (KE) for that.
- Alice transmits this ciphertext to Bob using an insecure channel (C) (e.g., The Internet).
- An attacker (Eve or Mallory) can listen to or modify the data on this insecure channel.
- When the message gets to Bob, he must use a decryption algorithm (D).
- The decryption algorithm needs a decryption key (KD) to decrypt the plaintext.
- The decryption algorithm decrypts the ciphertext back into plaintext using the decryption key.
- Bob can read the message now after decryption.
So the cipher encryption function looks like this:
The encryption algorithm (E) needs the plaintext (M) and the encryption key (KE) to get the ciphertext (C):
E(M, KE) = C
The cipher decryption function looks like this:
The decryption algorithm (D) needs the ciphertext (C) and the decryption key (KD) to decrypt the ciphertext back into plaintext (M):
D(C, KD) = M
What is the difference between symmetric encryption and asymmetric encryption?
- The main difference between symmetric and asymmetric algorithms is that in the symmetric algorithms the key to encrypt is the same as the key to decrypt, so (KE = KD). In asymmetric algorithms these keys are different, so (KE != KD).
- In the asymmetric algorithm, each person has his own public and private key. The public key can be shared with all communication partners.
- The key used for encryption (KE) in the asymmetric algorithm is the public key (it should be Bob’s public key) and the key for decrypting (KD) is the private key (Bob uses his private key to decrypt). It should also be hard to get the private key from the public key, and the public key can only encrypt but not decrypt the message.
What are the advantages and disadvantages of symmetric and asymmetric cryptosystems?
The advantage of symmetric cryptosystems is that they are fast and can encrypt and decrypt large amounts of data well and efficiently. The disadvantage is that you have to exchange the keys between all communication partners.
The advantage of asymmetric cryptosystems is that it solves the key exchange problem for symmetric cryptosystems. So it is used for the key exchange of the symmetric cryptosystems. The disadvantage of asymmetric cryptosystems is that they are slower than symmetric cryptosystems, so they are mostly not used for encryption and decryption of large amounts of data.
What makes a cryptosystem strong and safe?
There are two properties that make a cryptographic system secure:
Confusion: There should be a complex relationship between the key (K) and the plaintext (M). So it should be hard to get the key (K) from plaintext (M) and ciphertext (C).
Diffusion: There should be a complex relationship between the plaintext (M) and the ciphertext (C). So it should be hard to get from ciphertext (C) to plaintext (M) without knowing the key (K).
How can a hacker attack cryptosystems?
There are various methods that a hacker can use to attack cryptosystems:
Ciphertext-only attack: The hacker has access to cyphertext messages (C) only and he has no information about the algorithm or the key.
Known and Chosen plaintext attacks: The hacker knows or chooses pairs of plaintext (M) and Ciphertext Ciphertext (C).
Brute force: The hacker tries all keys (K) from the keyspace. This method always works but requires very powerful computers to run the attack. It could also take sometimes millions of years before the key could be cracked.
Purchase-key attack: In this attack, keys can be stolen if the attacker blackmails someone to get his key or he uses social engineering to get the key.
What are the goals of Cryptography?
The three most important goals for protecting information security in IT systems are:
Authenticity: Attackers should not be able to send messages and pretend to be Alice or Bob.
Confidentiality: attackers should not be able to read the plain text (secrecy).
Integrity: Attackers should not be able to modify, alter, or delete Alice or Bob’s messages.
What are hash functions?
Hash functions are functions that take input of any length and produce an output of a fixed length (e.g. SHA-256). The hash functions can be calculated efficiently, which means a hash of an input size (n) should have a running time of O(n).
Once you have hashed a value x, you cannot reverse the process and unhash the H(x). So that means if you have a hash value H(x), the only way to find x is by trying to hash all possible values (H(a), H(b), H(c)…) and then compare the output with H(x).
Hash functions are typically used to store passwords in a database.
There are two important properties that are very important for hash functions:
Collision-resistance: A hash function is collision-resistant if and only if there are two input values, x and y, with x != y, then it should be almost impossible to obtain the same hash function (H(x) != H(y) should be satisfied).
If(x!=y){
H(x) != H(y);
}
Hiding: If we know the hash value y for an input x (y = H(x)), then there shouldn’t be an easy way to find out what value x has by just knowing y.