How to find vulnerabilities in systems using Nmap
Vulnerability assessment is very important when it comes to IT security and penetration testing.
Vulnerability assessment is the key to conducting a penetration test and involves the use of various tools to find known vulnerabilities in the target system. One of the most important tools is Nmap.
Nmap can perform many tasks, but it is mainly used as a port scanner to find vulnerabilities in systems. In this tutorial, we will show you how to find vulnerabilities in systems by using Nmap.
How to install Nmap?
You can install Nmap in Windows and Unix-based systems. The installation is different for both systems, but also simple:
How to install Nmap on windows?
To install Nmap on the Windows system you need to:
- Go to the Nmap website
- Download the Nmap Windows version
- Install the executable Windows version
How to install Nmap on Debian-based systems?
Sometimes we need to install Nmap with all the required dependencies for Debian-based systems manually. We can do that in two simple steps:
- Open the terminal
- Type the following command
sudo apt install nmap
What port states are there in Nmap?
You may think that there are logically just two states for a port open or close. Unfortunately, there are more statuses we will see regarding ports status:
- Open port: Means that an application on the target machine is actively listening for connections on this port.
- Closed port: Means there is no application actively listening for connections on this port. However, the port could open up at any time.
- Filtered port: Nmap cannot determine if the port is open or closed because either a filter, a firewall, or some kind of blocking system is blocking the port.
- Unfiltered port: There is a response to Nmap probes on the port; however, Nmap can’t determine whether the port is open or closed.
- Open/Filtered: port: The port is either filtered or open.
- Closed/Filtered: The port is either filtered or closed.
Sometimes Nmap needs root privileges to run some commands. I will run all commands with root privileges to avoid wasting time by running this command on kali linux:
sudo su
In this Tutorial I am using Ubuntu so I will have to write sudo before each command.
How to do a basic scan with Nmap to know if a device is active on a network?
It is known that pentesters mostly use netdiscover to know which devices are active in the network. But that is also possible with Nmap, the only difference is that Nmap needs the target IP address. Let’s run the command that does a basic ping scan on a single target:
sudo nmap -sn (target IP address)
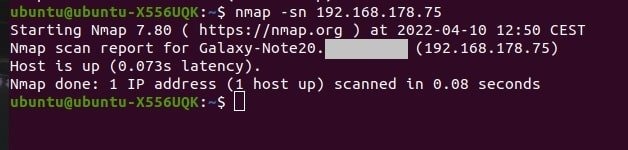
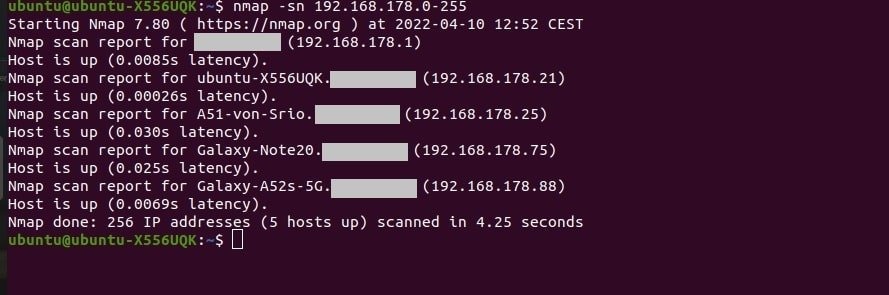
If we want to ping the entire subnet and find out what devices are active. We need to know the target IP subnet:
sudo nmap -sn (target IP subnet)
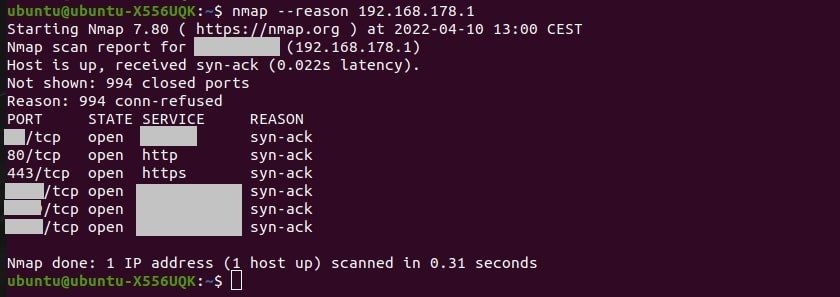
How to do the Nmap Reason Scan?
Sometimes you want to know why Nmap reports a port as open. The solution to this problem is to run the Nmap Reason Scan:
sudo nmap --reason (target IP address)
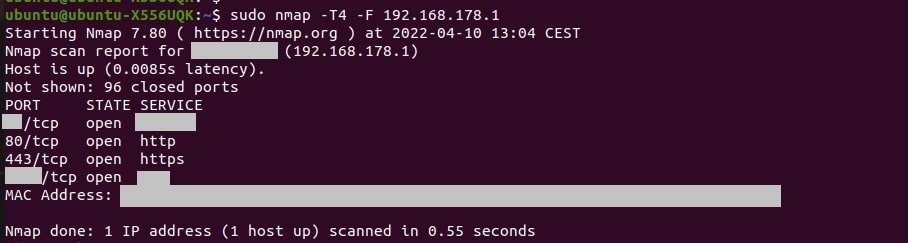
How to do a quick port scan with Nmap?
After knowing the target IP address you might want to run a quick and detailed scan with Nmap to know the opening ports and services running on them.
sudo nmap -T4 -F (target IP address)
How to detect the target operating system with Nmap?
Nmap is also capable to detect the operating system version that the target is running on their device:
sudo nmap -O (target IP address)
How to do intense port scan with Nmap?
If you want to run multiple scans with one command you may want to do an intense scan. This intense scan will scan open ports, do service enumeration, and will also detect the operating system of the target.
sudo nmap -T4 -A -v (target IP address)
How to know what IP protocols are supported by the target with Nmap?
Run the following command:
sudo nmap -sO (target IP address)
How to do Service Enumeration with Nmap?
If you want to enumerate the services associated with the ports you may want to do a service enumeration and know what service version is running on a port with Nmap:
sudo nmap -sV (target IP address)

How to do UDP port scan with Nmap?
You may not be interested in the TCP scan and would like to run a UDP port scan instead.
This scan takes much longer than the TCP scan so be prepared to wait over half an hour if you want to scan all UDP ports.
sudo nmap -sU (target IP address)
How to scan specific ports with Nmap?
Scanning all ports can take a long time and you only want to scan ports 50 to 100. This is also very easy with Nmap. Let’s do an example with a UDP scan because the UDP scan takes a lot of time.
sudo nmap -sU -p 50-100 (target IP address)
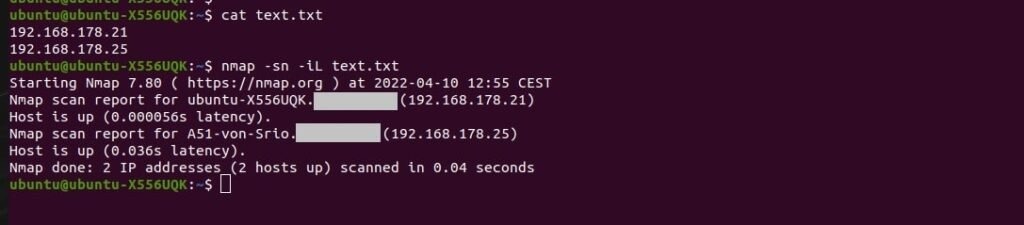
How to scan in Nmap using an input file?
If we want to scan a very large number of IP addresses, we need to put all these IP addresses in a text file and run a scan for the IPs in this text file:
sudo nmap -sn -iL (file path)
Nmap Scripts
We can run scripts with Nmap which will help us to get more information about the target.
Example for scripts:
Some HTTP scripts:
nmap --script http-title (target IP Address)
nmap --script http-methods (target IP Address)
nmap --script http-wordpress-enum (target IP Address)
nmap --script http-devframework (target IP Address)
Some FTP scripts:
nmap --script ftp-vsftpd-backdoor (target IP Address)
nmap --script ftp-brute (target IP Address)
Some MySQL scripts:
nmap --script mysql-info (target IP Address)
nmap --script mysql-empty-password (target IP Address)
nmap --script mysql-users (target IP Address)
Some SSH Scripts:
nmap --script ssh-brute (target IP Address)
nmap --script ssh-hostkey (target IP Address)
nmap --script ssh-publickey-acceptance (target IP Address)
There are much more scripts you can find online for other services like SMTP, SMB, DNS, etc.